statcert: a new tool to identify the type of X.509 certificates and their revocation status
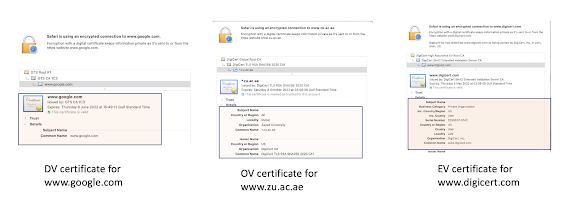
Today three types of certificates are used by the web: DV, OV, and EV. The DV certificates only ensure that the certificate owner has the right to control the domain name. Still, it doesn't provide any information about the owner's identity. On the other hand, the OV certificate lets one know that the owner has the right to use the domain name, but it gives more information about the domain name's owner, such as the organization name and the country. Finally, the EV certificates are similar to OV, but they provide more information about the owner, and the verification procedures of the owner information are more strict.
Web users have to trust a website that uses an EV certificate more than a website that uses a DV or OV certificate. However, it is difficult for a web user to distinguish these certificates as the web browsers have decided to remove all the visual indicators for EV certificates.
We have built a new tool called statcert that allows us to know the type of X.509 certificate used by any website. The tool can be installed from this GitHub repository :
https://github.com/SamerW/statcert
This tool can also be used to check the revocation status of certificates. Some web browsers, such as Google Chrome, don't check the certificate status for OV and DV certificates. A user can use our tool to check the status of any certificate.
In addition, our tool can allow us to understand the trend of the web PKI market to know the types of certificates that are the most dominant. The tool automatically downloads the list of one top million websites from Tranco List (https://tranco-list.eu) and generates a report to give the number of EV, OV, and DV certificates found on these websites. The number of websites to check can be reduced to any value less than one million so that the user can reduce the time needed to generate the report. We are using Tranco List and not Alexa of Amazon because Tranco List provides a more reliable list that is hardened against manipulation.
I give here some quick examples:
statcert google.com --ocsp: allow to download the certificate of the web server of google.com domain and check its ocsp status (whether the certificate is revoked or not)
I can use the tool to check different domains simultaneously, but I will add the -v option that allows me to see the report generated for the three domains. Here is one example:
statcert -v google.com zu.ac.ae facebook.com --ocsp
Finally, I use the tool to check the types of certificates for the top 20 websites according to Tranco List. The generated report shows that only one website uses an EV certificate, while 13 websites use OV certificates and 5 websites use DV certificates.





Comments
Post a Comment